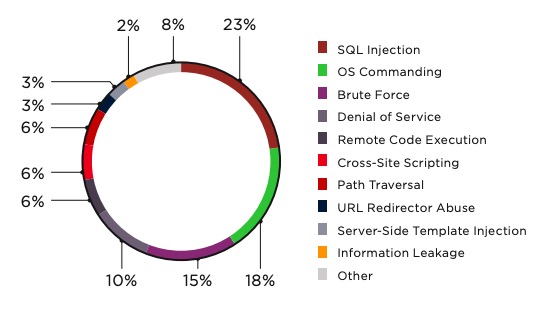
Casinos have been a target for crooks since the early days of organized gaming. Criminals tend to follow the money, and with serious money changing hands in the casino business, this has been a natural fit for centuries. In fact, so much so that casinos have become synonymous with high levels of security, hiring teams of loss prevention officers in and around the casino floor to limit damage. A prime example is Vulkan Casino, which offers a no deposit Vulkan bonus that greatly increases your chances of winning.
As casinos do more and more business online, the threat from scammers remains the same, if not increased before – only the landscape has changed. So instead of chip-switching scams, hidden earpieces and hacking, we’re seeing new methods of:
- DDoS attacks;
- Game hacks;
- Fraud using user accounts;
- Code injection;
- SQL Injection;
- Command injection;
- XSS injection;
- XPath injection;
- Mail command injection;
- CRLF injection;
- Host header injection;
- LDAP injection.
Cybersecurity is becoming a growing problem for casino operators, if not more important than security at offline casinos. With a more compressed target and a million and one ways to potentially infiltrate digitized systems, casinos must be more proactive than ever to protect their platforms.
Our gambling experts recommend that you familiarize yourself with the reliable institutions in terms of security in the published ranking of the Best Casino Websites for Canadian players and be sure that we have chosen only legal online casinos with modern protection.
Basic types and types of cyber attacks on infrastructure
It usually doesn’t matter whether your infrastructure is on-premises or in the cloud. If the data you transmit has value, someone will want it. Attackers’ actions can be divided into two main types – distributed and targeted attacks.
Distributed cyber attacks are the use of a botnet and target a large number of users and company resources simultaneously. As a rule, these attacks use leaked databases of organizations and users.
Targeted attacks (APTs) are a pre-planned “attack” against a specific company or infrastructure. In these incidents, the attacker not only gains access to internal resources, but also remains on the company’s network until they are discovered, which can be days, months, or even years. Targeted attacks are carried out by hackers with high technical competence. They use automated tools, determine attack vectors, exploit 0-day vulnerabilities and certain system features based on their experience.
Cyberattacks pose a danger to both ordinary users and businesses. In both cases, the consequences can be not just unpleasant, but critical. According to 2020 statistics provided by Acronis, DDoS attacks, phishing and videoconferencing attacks topped the list of cyber threats. However, other types of attacks cause a lot of problems for businesses and ordinary users alike. Attackers blackmail messenger users with bots, break into the network via QR codes and exploit vulnerabilities in legal network settings or encryption, as well as resort to the classics of the genre – brute force attacks. In order to better understand cybercriminals’ actions, it is necessary to know what types of attacks on infrastructure exist and their key features.
DoS & DDoS attacks
Distributed denial-of-service attacks are implemented by using multiple compromised computer systems as sources of attack traffic. These attacks clog systems with a large number of requests, resulting in reduced bandwidth and systems becoming overloaded and unavailable. In essence, a DDoS attack is like an unexpected traffic jam clogging a highway.
Fishing attacks
Fishing attacks are based on the use of emails that can be disguised as legitimate messages from various companies. In such a fake message, attackers may offer to follow a link, download an infected file or ask to hand over a user’s confidential data – logins, passwords and bank card account numbers.
Brute-force attacks
Brute-force attacks are a fairly simple method of infiltrating an infrastructure and represent “guessing” user accounts. Some attackers use applications and scripts as brute-force tools that try many combinations of passwords to bypass authentication processes. If the password is weak, attackers will only need a couple of seconds, so businesses should enforce a strict password policy.
Bots
This is a software robot that mimics or replaces human behavior and performs simple tasks at a rate that exceeds user activity. Some bots can be useful, and their actions are aimed at supporting users, but there are also malicious ones. For example, they are used to automatically scan websites and look for vulnerabilities, as well as to perform simple cyberattacks.
Man-in-the-Middle (MITM) attack
In this type of attack, the cybercriminal becomes a “third party” and allows all web traffic to pass through himself. At this point, the potential victim is completely unaware of it, which means that the attacker gets all the credentials he needs to log in. The information obtained can then be used to steal corporate data or unauthorized fund transfers.
What are the risks of hacking or external attack?
Hacking is a major risk for online casinos from cyberattacks, and it is critical that operators take measures to prevent backdoor loopholes and exploits from being accessed by criminals. If a casino is vulnerable, it could potentially disclose its customers’ personal data to fraudsters, who could then use that data to steal – directly or indirectly from the customer or the casino.
There may also be a more direct risk of payment information falling into the wrong hands – such as credit card information, which could easily be seized by hackers to cause significant harm to the holder.
In addition to casinos’ responsibility to do everything they can to protect their customers, there are several other significant reasons why casinos should step up their operations and take steps to protect against these threats.
For casino operators in Canada, GDPR rules require public disclosure of any data leaks almost as soon as they become apparent, which is a PR disaster waiting to see if any data has actually been compromised. In addition, there could be licensing problems for those who are found to have done so.
And, of course, it does nothing to build trust between the customer and their casino if online casinos are vulnerable to this type of attack. This can have long-term consequences for casino operators, and as we’ve seen in the case of high-profile hacks over the years, there’s a real potential to destroy a trusted casino brand.
Unfortunately, this is not a static picture, as risks and protections in cybersecurity are constantly changing and evolving. As a consequence, it is imperative that casinos take risk seriously and take steps to protect against these threats, both now and in the future.
Integrity of game data and source code
There is another important point of trust here for casinos. The online casino operator is as good as its games, and if hackers can compromise the integrity of the gaming experience, there is a risk of undermining the broader trust in the integrity and legitimacy of online gambling platforms.
Players want to know that they are participating in a fair game with a legitimate chance of winning. But if hackers can gain access to exploits in the gaming software, the results for players and for the casino could be disastrous. Not only does this compromise the integrity of games that customers trust, but it also opens up casino operators to big losses when their spins are turned.
Again, it comes down to being one step ahead of the attackers, which is easier said than done. The only option casinos and game developers like Microgaming and NetEnt have is to invest in cybersecurity talent and regularly check and verify gaming software so that there are no obvious pathways. But with ever-changing gates, it’s an ongoing and uphill battle.
Prevent database and user information leakage
In addition to the safety of their customers, casinos must also take care of themselves. Loss prevention is worth millions to the online gambling sector, and it’s not hard to see why. With an insecure website or mobile platform, casinos are potentially exposed to significant losses. And in some cases, those losses can pile up in the blink of an eye.
An ineffectively secured casino is similar to leaving a bank vault unlocked, and it may be one of the biggest financial risks to casino operators due to cybersecurity issues. Disabling leaks in the system is necessary for operators to preserve their financial integrity and ensure that crooks don’t have a day job at their expense.
Use of modern encryption technology
Technologies such as Cloudflare can protect against DDoS attacks by directing and filtering traffic through the cloud network, and even a simple VPN can make you a harder target. CAPTCHA is another popular solution that helps reduce the damage from DDoS attacks because it offers every user a simple solution.
DDoS attacks use bots, and while no single solution provides 100% protection, each one forces hackers to use more bots, make them smarter, or keep the attack longer in order to succeed. All of this makes the attack attempt harder and more expensive.
The best defense against SQL injection is to encrypt databases. These attacks mostly target companies with outdated or poor infrastructure, so if you’ve invested in security, the risk of damage is greatly reduced.
How to be safe online
Not a day goes by without headlines about a new online scam, a hacking method, or a massive leak of sensitive data. If this has happened to you, you can fully understand the anger, panic and frustration this can fill you with. For those who are already unfamiliar with the online world, getting hacked or using the Internet can cause them to avoid digital platforms altogether, which can be very isolating these days.
The problem of online fraud, hacking and theft will never go away – in the past, people have always pulled the same scams, just over the phone or through the mail. While hacking and scams will never stop, you can learn how to protect yourself, your assets and your information and help your loved ones stay as safe as possible online.
Stop, think and wait before you send the data
Scams and hacking attempts come in many shapes and sizes, but one of the most popular are phishing emails. Phishing emails are essentially random emails prompting you to click a link. Once you click the link, you may be redirected to a page that appears to be official, and you will be asked to enter some personal information, which the scammer will then use to steal additional information or money.
We are notoriously bad at identifying when an email is phishing, but there are some obvious signs: look at the email domain, check for spelling errors in the domain and the rest of the email, look at the link itself to see if it seems odd, and ask yourself if the email creates a sense of urgency. If the email has any of these telltale signs – be careful! You can report it as phishing or ask a friend’s opinion, but don’t click on the link.
It requires you to stop, think, and wait. Scammers want you to react suddenly, rashly, and click the link without thinking. So much of what we do online we do without thinking, and you can hardly blame us for that! When you work at your computer all day, it can be difficult to carefully examine every email.
Play online games safely
One of the most popular industries for hackers and scammers is the online gambling and sports betting industry. There are thousands of secure betting sites and platforms, but some scammers have created fraudulent online casinos solely to steal unsuspecting users’ personal information and money.
Secure online casinos operate all over the world. Canada is one of the countries that really takes its cybersecurity seriously, and the country has introduced detailed data protection legislation specifically to protect its citizens. Germany is a great example for all industries because they take cybersecurity and protection very seriously.
Canadian players look for the best no deposit casino bonuses, for example on various online gambling sites and every online casino will experience the same level of care as online casinos have to adhere to the same principles and take the same precautions as other online service platforms. Canadian users are advised to be aware of the casinos they use, including the licensing that is in place for each casino. This is a responsible model that countries around the world should adopt to increase digital security.
Be careful when communicating with suspicious users
When you communicate with someone online, it’s easy to let your guard down, especially if you feel like you’ve made a connection. Nevertheless, you need to be actively cautious and mindful of safety when communicating with others online. In practice, this means that you should not share personal information with strangers online and be careful about who you communicate with. You never know who someone really is.
Safety is the main thing
Another great way to protect your information and finances online is to take passwords seriously. Try to come up with great passwords that are hard to guess – with numbers, special characters and the occasional use of capital letters. Users should also opt for two-factor identification where possible. Two-factor identification means that you can’t access a particular online account, such as email or e-wallets, without first entering your password and then confirming that you’re logged in either by entering a code that was sent to you in a text message or by using an app. confirm.
Vigilance at online casinos is never redundant
If you have been hacked and lost money or personal information, you probably feel helpless, frustrated and overwhelmed with anger. Before you do anything, take time to reflect on what happened and accept the fact that everyone is either being hacked or having something stolen at one point or another.
The Canadian CCCS has great advice on what to do if you think you’ve been scammed, as well as how to report a scam. Don’t blame yourself or think you’re stupid, it happens to literally everyone. Just follow the CCCS guidelines and tell your friends and family to beware, too.