The healthcare sector is rapidly embracing digitization providing immense opportunity. But it also brings new risks relating to data security. Every element of such a complex system containing medical devices presents a potential hazard — a weak spot that cybercriminals will seek out and try to exploit.
That’s why confidence in healthcare data systems and medical devices is indispensable and must be designed from the beginning. One of the solutions to guarantee high medical systems protection is the adoption of specialized security frameworks.
This post will guide you through the most popular framework examples and a step-by-step approach to their incorporation.
What Is The Feature of Cybersecurity Frameworks for Healthcare
Jumping headlong into a new tech solution without knowing the basics is a mistake. So let’s consider the essence of such a security layer and why to employ it in telehealth.
Cybersecurity framework or CSF is a mix of values and practices designed to protect corporate systems and communicate security hazards. In other words, security frameworks provide techniques for combating safety threats and assist in supervising confidential info in a way it’s protected. It has a considerable broad appeal to many organizations and can be used across multiple areas, including healthcare.
Why apply frameworks in healthcare?
Telemedicine deals with a significant number of sensitive records (derived from multiple devices), becoming a tidbit for cybercriminals. That’s why healthcare entities face challenges coping with rising cyber threats and data leakage. A large-scale attack on medical organizations may block their operations for medical services. That’s the primary reason clinics integrate security software into their IT systems.
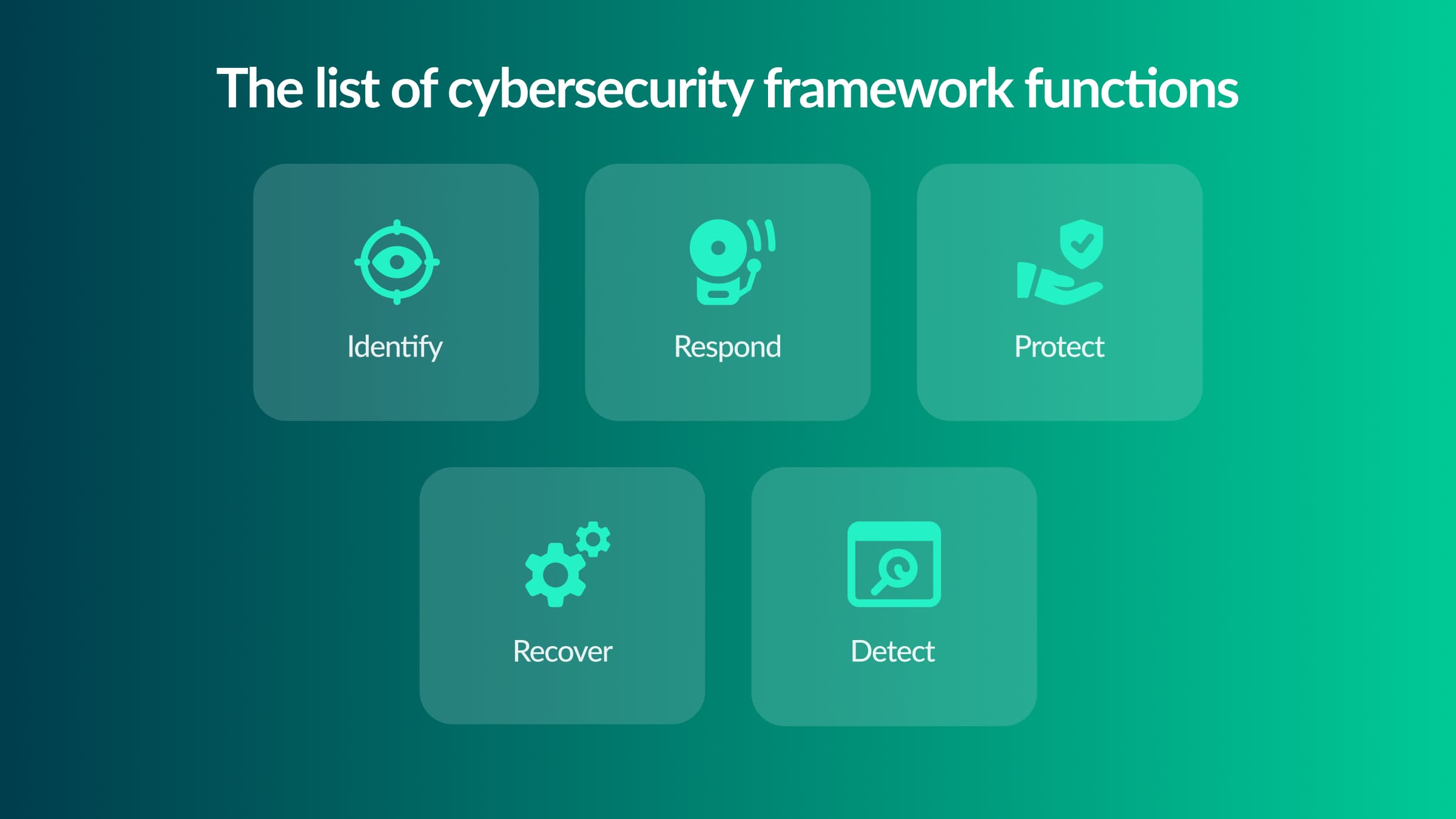
But how exactly can CSF help hospitals address security matters? They allow for detection, safeguarding, reaction, and recovery from the consequences of cybercrime. It’s not considered strict rules for healthcare businesses, but directions of efficient security information systems.
5 Top Security Frameworks for Healthcare
Here is the list of the most prevalent legislation and frameworks that medical entities should account for when building their data security strategy.
NIST CSF
It is not the certification framework; its criteria were written with the industry’s best expertise for administering cybersecurity risks in mind. And this enables the alignment across various IT compliance frameworks like HIPAA. These criteria are also scalable, making the framework easily tailored to business-specific needs. It initially determined security rules and privacy standards for public and government organizations, but now the standards apply to non-government institutions, including the healthcare sector.
ISO 27000 Series
ISO/IEC 27001 is a broad support international standard that provides a set of regulations for managing data security. This is a systematic approach composed of experts, processes, and technology that help organizations protect and maintain all corporate information through risk management. It focuses on covering three aspects of data:
- Confidentiality (information isn’t disclosed to unauthorized users)
- Integrity (data is utter and accurate and safeguarded from corruption)
- Availability (info is accessible and usable by authorized users as required)
HITRUST
The HITRUST Association is a private firm that cultivates, maintains, and provides access to valuable techniques to facilitate the incorporation of robust data security programs in all-sized companies. HITRUST released the HITRUST CSF, which implies a comprehensive framework that helps healthcare establishments improve information risk management and compliance programs. The high trust CSF is based on nationally and internationally accepted security and privacy-related regulations, such as HIPAA, NIST, and PCI, to build a controlled environment for security control.
COBIT CSF
This methodology provides guidance on how to organize IT-related activities across all business processes properly and reliably. It assists firms in addressing gaps between technical concerns, business risks, and control demands.
Here are the critical parts of this framework:
- Process model helps corporations comprehend the nature of all the activities that relate to IT as well as how to arrange them in a way they’re reliably performed (e.g., managing changes)
- Best practice implies providing guidance on what to do in each of these processes in alignment with recognized good practice. It allows for ensuring the proper performance of IT-related activities.
- Management tools allow companies to measure the quality of those processes using capability maturity techniques. So management can tell whether the activity is at the level required for a given situation.
Critical Security Controls
These are the international principles and proven methodologies for protecting the IT landscape and corporate data against omnipresent hackers’ invasions. These accepted regulations are constantly polished and audited by global tech minds. The significant advantage of these rules is that they prioritize the actions and concentrate on the critical ones that extremely minimize the risk rate.
Things to Consider Before Adopting Healthcare CSF
Now, let’s see what points should be accounted for before implementing security frameworks into your corporate environment.
Define business needs
The primary step includes determining the key goals and setting business priorities. That’s needed to develop an effective data security strategy and identify the systems and tools enlisted in the chosen process.
Recognize approaches to management
Initially, the enterprises access resources they possess, select the appropriate directive, and seek credible sources. Then, they estimate the overall danger and determine the white spot in their current tools and programs.
Evaluate the risks
Before CSF adoption, appraising the IT landscape threat level is vital. That means scrutinizing the prospects for security breaches and the effects they may provoke.
Make a profile
Medical establishments make a thorough risk assessment and determine their present state. The primary objective is to receive a deep insight into current security threats (those that may appear due to security violations). Thus, all the hazards and weaknesses should be detected and recorded.
Define and order the gaps
After recognizing the perceived dangers and their outcomes, it’s time to proceed to safety holes analysis. That’s required actual vs. the target outcomes comparison. For instance, making a heat map will help you emphasize the number-one focus area.
Enforce a series of measures
Lastly, a precise knowledge of potential safety hazards, preemptive measures, objectives, and holes analysis backed up with a list of required acts will allow healthcare establishments to adopt these protection measures.
Find a reliable IT partner
Before cybersecurity frameworks incorporation, it’s significant to choose an experienced custom healthcare software development company. This way, you’ll be ensured all the peculiarities will be taken professionally. There are many hiring platforms available that can assist you in finding competent experts in tune with your budget, time, and expectations. Many entrepreneurs consider outsourced development when it comes to developing telehealth projects. This model entails cooperation with a tech partner remotely. By doing so, you receive a composed team of certified experts needed to integrate CSF into your IT ecosystem. As for the telemedicine app development cost, the price depends on the specialists’ level of expertise and the vendor’s location. For example, software engineers charge $150 to $250 per hour in the US, while consulting rates in North Europe are $50-$75.